欢迎大家赞助一杯啤酒🍺 我们准备了下酒菜:Formal mathematics/Isabelle/ML, Formal verification/Coq/ACL2, C++/F#/Lisp
灰狐安全
小 (→DevSecOps) |
小 (→数论密码学) |
||
| (未显示1个用户的87个中间版本) | |||
| 第2行: | 第2行: | ||
==简介== | ==简介== | ||
| − | + | 安全产品、安全咨询、安全审计、安全服务 | |
| + | |||
| + | [[c programming language|C]]/[[C++]]/[[Go]] 是主力语言,跟进咨询核心开源安全软件,如:[[OpenSSL]], [[GnuTLS]], [[Let's Encrypt]], [[OPNsense]], [[pfSense]] | ||
| + | |||
| + | [[Blockchain]] Security & [[Ethereum]] & [[Solidity]] Smart Contract Audits | ||
| + | |||
| + | 软硬件安全、可靠性、[[Formal verification|形式化验证]]服务是核心,[[OCaml]]([[Coq]]) & [[Haskell]]([[Agda]]) 是核心语言和形式化能力。 | ||
| + | |||
| + | [[Cryptol]] [[Cryptography]] language,支持证明(:prove 命令)所有可能的输入的谓词(:check 命令)。 | ||
==愿景== | ==愿景== | ||
Vision:Building a comprehensive open source security platform. | Vision:Building a comprehensive open source security platform. | ||
| + | |||
| + | [https://c4pr1c3.github.io/cuc-ns/ds-security/what.html 数据驱动安全] “Mastering data. Securing the world”(掌控数据,保护世界) | ||
==路线图== | ==路线图== | ||
| 第26行: | 第36行: | ||
技术融合,交付更大价值的安全服务。 | 技术融合,交付更大价值的安全服务。 | ||
| + | |||
| + | [https://forge.huihoo.com/news/643 对数据库、存储、数据安全外包业务的一些思考] | ||
| + | |||
| + | ==SSL/TLS/Crypto== | ||
| + | 对 SSL, [[TLS]], [[Cryptography]] 和 [[Let's Encrypt]] 的持续跟进。[[文件:gnutls-logo.png|GnuTLS]] [[文件:Openssl.png|OpenSSL]] [[文件:LibreSSL-logo.jpeg|LibreSSL]] [[文件:Letsencrypt-logo.png|Let's Encrypt]] | ||
| + | |||
| + | ==安全基金会== | ||
| + | [[文件:OWASP-logo.png|right|OWASP]] | ||
| + | [[文件:OpenSSF.png|right|OpenSSF]] | ||
| + | |||
| + | 持续跟进: | ||
| + | *[[OWASP]] | ||
| + | *Open Source Security Foundation ([[OpenSSF]]) 尤其 Security Scorecards 项目。 | ||
| + | |||
| + | ==数论密码学== | ||
| + | [[Computational mathematics|计算数学]]、数论、[[Cryptography|密码学]]是安全基石 | ||
==DevSecOps== | ==DevSecOps== | ||
| 第42行: | 第68行: | ||
==OSINT== | ==OSINT== | ||
Open Source Intelligence ([[OSINT]]) 开源情报 | Open Source Intelligence ([[OSINT]]) 开源情报 | ||
| + | |||
| + | ==Haskell== | ||
| + | [https://galois.com/ Galois] Trust your most critical systems, Galois’s open source verification tools ([https://saw.galois.com/ SAW] [[Cryptol]] and [https://crux.galois.com/ Crux]). | ||
| + | |||
| + | [[cryptol|Cryptol Cryptography language]], Ivory E[[DSL]], Software Analysis Workbench (SAW) 带来全新的安全思维。 | ||
| + | |||
| + | ==OCaml== | ||
| + | 静态分析、代码质量、代码安全 | ||
| + | |||
| + | [https://github.com/facebook/infer Infer] in the "static analysis world", [[OCaml]] is one of the most popular languages. | ||
| + | |||
| + | [https://github.com/mirleft/ocaml-tls ocaml-tls] [[TLS]] in pure OCaml. | ||
| + | |||
| + | ==Identity== | ||
| + | [[文件:ory-logo.png|right|Org]] | ||
| + | [[文件:Keycloak-logo.png|right|Keycloak]] | ||
| + | Open Source [[identity management|Identity and Access Management]] | ||
| + | *[[Keycloak]] | ||
| + | *[[ory|ORY]] identity platform | ||
| + | *[[狗狗通行证]] | ||
| + | |||
| + | ==区块链== | ||
| + | [[blockchain|区块链]]和数字货币安全 | ||
| + | |||
| + | 区块链和智能合约的 [[Formal verification]] | ||
| + | |||
| + | ==操作系统== | ||
| + | [[文件:pfsense-logo.jpeg|pfSense]] [[文件:OPNsense-logo.png|OPNsense]] [[文件:VyOS-logo.png|VyOS]] [[文件:DANOS-logo.png|DANOS]] | ||
| + | |||
| + | 基于 [[FreeBSD]] , [https://vyos.io/ VyOS] 的防火墙、路由器和NAS、软件定义存储是核心。 | ||
| + | *[[OPNsense]] & [[pfSense]] Firewall, VPN, and Router | ||
| + | *[[Linux]] [https://grsecurity.net/ grsecurity] 安全补丁集 | ||
| + | *[https://hardenedbsd.org/ HardenedBSD] 主要目标是 grsecurity 的重新实现, [https://git.hardenedbsd.org GitLab 仓库] | ||
| + | *[[FreeBSD]] + [[LLVM]] | ||
| + | 基于 [[Vyatta]] 的解决方案 | ||
| + | *[https://vyos.io/ VyOS] is an open source router and firewall platform based on [[Debian]] GNU/Linux, based on [[Vyatta]]. | ||
| + | *[https://github.com/danos DANOS] A Unified Network Operating System Driving Innovation Across the Networking Stack, based on [[Vyatta]]. | ||
| + | |||
| + | ==数据库存储== | ||
| + | [[文件:OpenZFS-logo.png|right|OpenZFS]] | ||
| + | *[[PostgreSQL]] | ||
| + | *[[MariaDB]] | ||
| + | *[[ScyllaDB]] | ||
| + | *[[OpenZFS]] | ||
| + | *[[FreeNAS]] | ||
| + | *[https://papers.freebsd.org/2020/pbug/vermaden-freebsd-enterprise-storage/ FreeBSD Enterprise Storage] | ||
| + | *[https://papers.freebsd.org/2021/eurobsdcon/gallatin-netflix-freebsd-400gbps/ Serving Netflix Video at 400Gb/s on FreeBSD] | ||
==项目== | ==项目== | ||
| + | [[文件:WireGuard-logo.png|right|WireGuard]] | ||
| + | [[文件:Wazuh-logo.png|right|Wazuh]] | ||
| + | [[文件:eBPF-logo.png|right|eBPF]] | ||
| + | *[[WireGuard]] | ||
*[[Open Policy Agent]] | *[[Open Policy Agent]] | ||
*[[Vault]] | *[[Vault]] | ||
| − | |||
*[[Wazuh]] 基于趋势科技的 OSSEC 构建(分支),[https://wazuh.com/migrating-from-ossec/ Migrating from OSSEC] | *[[Wazuh]] 基于趋势科技的 OSSEC 构建(分支),[https://wazuh.com/migrating-from-ossec/ Migrating from OSSEC] | ||
| − | *[[PKI]], [[CA]], [[TLS]] | + | *[[PKI]], [[CA]], [[TLS]], [[GnuTLS]] |
*[[LDAP]], [[Apache Directory]], [[OpenLDAP]] | *[[LDAP]], [[Apache Directory]], [[OpenLDAP]] | ||
*[[lego]] [[Let's Encrypt]] client and [[ACME]] library written in [[Go]]. | *[[lego]] [[Let's Encrypt]] client and [[ACME]] library written in [[Go]]. | ||
| − | |||
*[[StackStorm]] | *[[StackStorm]] | ||
| − | |||
*[[falco]] | *[[falco]] | ||
| + | *[https://github.com/OpenSC OpenSC] Open source smart card tools and middleware. PKCS#11/MiniDriver/Tokend | ||
| + | *[https://github.com/Yubico/yubico-pam Yubico Pluggable Authentication Module (PAM)] | ||
| + | *[https://github.com/Yubico https://github.com/ehids/ecapture eCapture] 通过 [https://ebpf.io/ eBPF] 捕获没有 CA 证书的 SSL/TLS 文本内容。 | ||
| + | 从3.18版本开始,Linux 内核提供了一种扩展的 BPF 虚拟机,被称为“extended BPF”,简称 eBPF。它能够被用于非网络相关的功能,比如附在不同的 tracepoints 上,从而获取当前内核运行的许多信息,eBPF 现在被应用于网络、跟踪、内核优化、硬件建模等领域。 | ||
| + | |||
| + | ==形式化验证== | ||
| + | 我们核心关注软件和硬件的完全功能正确性的[[Proof assistant|规范和验证]]。 | ||
| + | |||
| + | [https://deepspec.org DeepSpec] 是一个有关软硬件规范(软件应该做什么)和形式化验证的技术联盟,主要专注核心系统软件,如:操作系统、编程语言编译器和计算机芯片等。 | ||
| + | |||
| + | 我们关注的形式化验证/证明助手语言有:[[OCaml]] 编写的 [[Coq]]、[[Haskell]] 编写的 [[Agda]]、[[Common Lisp]] 编写的 [[ACL2]]。 | ||
| + | |||
| + | [https://github.com/project-everest/hacl-star HACL*] a formally verified cryptographic library(形式化验证密码学库)written in [[F*]] | ||
| + | |||
| + | [[Solidity]] [https://github.com/runtimeverification/verified-smart-contracts Formally Verified Smart Contracts] | ||
| + | |||
| + | ==安全合规== | ||
| + | [[文件:OpenSCAP-logo.png|right|OpenSCAP]] | ||
| + | *[[OpenSCAP]] 开源安全合规解决方案,NIST认证的SCAP 1.2工具箱。[https://csrc.nist.gov/projects/Security-Content-Automation-Protocol Security Content Automation Protocol (SCAP)] 安全内容自动化协议 | ||
| + | *[https://www.nist.gov/itl/executive-order-14028-improving-nations-cybersecurity/software-supply-chain-security-guidance Software Supply Chain Security Guidance] | ||
| + | *[https://slsa.dev/ Supply chain Levels for Software Artifacts, or SLSA (salsa)] | ||
| + | *[https://github.com/sigstore sigstore] Software Supply Chain Security | ||
| + | *[https://openssf.org/ OpenSSF] Open Source Security Foundation | ||
==服务== | ==服务== | ||
| + | * Formal Verification(形式化验证) for [[Blockchain]] & Smart Contracts and Software & Hardware | ||
| + | * [[Zero trust security model|Zero Trust Architecture]](零信任架构) | ||
* Security Analytics(安全分析) | * Security Analytics(安全分析) | ||
* Intrusion Detection(入侵检测) | * Intrusion Detection(入侵检测) | ||
| 第66行: | 第165行: | ||
* Regulatory Compliance(合规性) | * Regulatory Compliance(合规性) | ||
* Cloud Security Monitoring(云安全监控) | * Cloud Security Monitoring(云安全监控) | ||
| − | * [[Container]] Security(容器安全) | + | * [[Container]] Security(容器安全)[https://www.armosec.io/ Kubernetes Security] 风险分析、安全合规、RBAC可视化和image漏洞扫描 [https://github.com/cncf/tag-security CNCF Security Technical Advisory Group] |
* [[Database]] Security(数据库安全) | * [[Database]] Security(数据库安全) | ||
| − | * Mobile Security([https://owasp.org/www-project-mobile-security-testing-guide/ 移动安全]) | + | * Mobile Security([https://owasp.org/www-project-mobile-security-testing-guide/ 移动安全]) [https://github.com/OWASP/owasp-masvs OWASP Mobile Application Security Verification Standard (MASVS)] |
| + | |||
| + | ==运营支撑== | ||
| + | [[C Sharp|C#]] Web/API + [[C++]]/[[Qt]] 桌面 + [[PostgreSQL]] 数据存储是整个产品和技术体系的软件基础设施。 | ||
==图集== | ==图集== | ||
| 第78行: | 第180行: | ||
image:wazuh-architecture-server.png|Wazuh Server | image:wazuh-architecture-server.png|Wazuh Server | ||
image:wazuh-deployment.png|Wazuh部署 | image:wazuh-deployment.png|Wazuh部署 | ||
| + | image:cryptol-repl.png|Cryptol REPL | ||
| + | image:eBPF.png|eBPF | ||
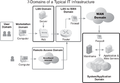
| + | image:seven-domains-of-a-typical-IT-infrastructure.png|典型IT基础设施的7个域 | ||
| + | image:security-systems.png|安全系统 | ||
| + | image:Defense-in-Depth.png|Defense in Depth | ||
| + | image:SDLC-SBOM.png|SBOM | ||
</gallery> | </gallery> | ||
==链接== | ==链接== | ||
| + | *[https://runtimeverification.com/ Runtime Verification Inc] We love formal methods | ||
*[https://owasp.org OWASP] | *[https://owasp.org OWASP] | ||
*[https://github.com/Hack-with-Github/Awesome-Hacking Awesome Hacking] | *[https://github.com/Hack-with-Github/Awesome-Hacking Awesome Hacking] | ||
| 第89行: | 第198行: | ||
[[category:security]] | [[category:security]] | ||
| + | [[category:identity]] | ||
| + | [[category:cryptography]] | ||
| + | [[category:firewall]] | ||
| + | [[category:router]] | ||
| + | [[category:formal]] | ||
[[category:OSINT]] | [[category:OSINT]] | ||
[[category:DevSecOps]] | [[category:DevSecOps]] | ||
[[category:huihoo]] | [[category:huihoo]] | ||
2024年11月13日 (三) 02:08的最后版本
灰狐安全
目录 |
[编辑] 简介
安全产品、安全咨询、安全审计、安全服务
C/C++/Go 是主力语言,跟进咨询核心开源安全软件,如:OpenSSL, GnuTLS, Let's Encrypt, OPNsense, pfSense
Blockchain Security & Ethereum & Solidity Smart Contract Audits
软硬件安全、可靠性、形式化验证服务是核心,OCaml(Coq) & Haskell(Agda) 是核心语言和形式化能力。
Cryptol Cryptography language,支持证明(:prove 命令)所有可能的输入的谓词(:check 命令)。
[编辑] 愿景
Vision:Building a comprehensive open source security platform.
数据驱动安全 “Mastering data. Securing the world”(掌控数据,保护世界)
[编辑] 路线图
DevSecOps + AISecOps 共筑下一代安全体系
1、DevSecOps 将安全置于 DevOps 整个生命周期 DevSecOps is a combination of Compliance Operations, Security Engineering, Security Science, and Security Operations.
2、AISecOps 人工智能自动化云安全服务 AISecOps as a holistic cloud operations and security management framework that covers the full-stack and incorporates AI to deliver automated response and incident management.
3、通过 PostgreSQL/Greenplum 建立分布式数据仓库 集中数据存储 机器学习和深度学习下沉至数据库 数据库内建机器学习和人工智能算法:一切皆 SQL
商业模式:安全服务具有连续性、持续性,企业每年都要交纳的服务费。
应用场景:如:基于日志的入侵检测分析、利用MADlib图算法检测异常行为
技术融合,交付更大价值的安全服务。
[编辑] SSL/TLS/Crypto
对 SSL, TLS, Cryptography 和 Let's Encrypt 的持续跟进。



[编辑] 安全基金会
持续跟进:
[编辑] 数论密码学
[编辑] DevSecOps
DevSecOps 通过自动检测和修复漏洞并免受目标性攻击和自动攻击程序的影响,
无需扫描或者调度,让软件能够自我防护。就像给你的应用程序打了疫苗。
应用场景:
- 自动进行渗透测试以优化资源
- 安全团队与敏捷(Agile) & 开发运营(DevOps)保持同步
- 安全即规范,开发速度更快、构建更安全、无时无刻的监测
- 攻击监测 = 应用安全监测(ASM)持续的可见性、应用智能、迅速响应
- 云安全,安全可扩展
- 帮助企业满足特定的安全合规性标准
[编辑] OSINT
Open Source Intelligence (OSINT) 开源情报
[编辑] Haskell
Galois Trust your most critical systems, Galois’s open source verification tools (SAW Cryptol and Crux).
Cryptol Cryptography language, Ivory EDSL, Software Analysis Workbench (SAW) 带来全新的安全思维。
[编辑] OCaml
静态分析、代码质量、代码安全
Infer in the "static analysis world", OCaml is one of the most popular languages.
[编辑] Identity
Open Source Identity and Access Management
[编辑] 区块链
区块链和数字货币安全
区块链和智能合约的 Formal verification
[编辑] 操作系统
基于 FreeBSD , VyOS 的防火墙、路由器和NAS、软件定义存储是核心。
- OPNsense & pfSense Firewall, VPN, and Router
- Linux grsecurity 安全补丁集
- HardenedBSD 主要目标是 grsecurity 的重新实现, GitLab 仓库
- FreeBSD + LLVM
基于 Vyatta 的解决方案
- VyOS is an open source router and firewall platform based on Debian GNU/Linux, based on Vyatta.
- DANOS A Unified Network Operating System Driving Innovation Across the Networking Stack, based on Vyatta.
[编辑] 数据库存储
- PostgreSQL
- MariaDB
- ScyllaDB
- OpenZFS
- FreeNAS
- FreeBSD Enterprise Storage
- Serving Netflix Video at 400Gb/s on FreeBSD
[编辑] 项目
- WireGuard
- Open Policy Agent
- Vault
- Wazuh 基于趋势科技的 OSSEC 构建(分支),Migrating from OSSEC
- PKI, CA, TLS, GnuTLS
- LDAP, Apache Directory, OpenLDAP
- lego Let's Encrypt client and ACME library written in Go.
- StackStorm
- falco
- OpenSC Open source smart card tools and middleware. PKCS#11/MiniDriver/Tokend
- Yubico Pluggable Authentication Module (PAM)
- https://github.com/ehids/ecapture eCapture 通过 eBPF 捕获没有 CA 证书的 SSL/TLS 文本内容。
从3.18版本开始,Linux 内核提供了一种扩展的 BPF 虚拟机,被称为“extended BPF”,简称 eBPF。它能够被用于非网络相关的功能,比如附在不同的 tracepoints 上,从而获取当前内核运行的许多信息,eBPF 现在被应用于网络、跟踪、内核优化、硬件建模等领域。
[编辑] 形式化验证
我们核心关注软件和硬件的完全功能正确性的规范和验证。
DeepSpec 是一个有关软硬件规范(软件应该做什么)和形式化验证的技术联盟,主要专注核心系统软件,如:操作系统、编程语言编译器和计算机芯片等。
我们关注的形式化验证/证明助手语言有:OCaml 编写的 Coq、Haskell 编写的 Agda、Common Lisp 编写的 ACL2。
HACL* a formally verified cryptographic library(形式化验证密码学库)written in F*
Solidity Formally Verified Smart Contracts
[编辑] 安全合规
- OpenSCAP 开源安全合规解决方案,NIST认证的SCAP 1.2工具箱。Security Content Automation Protocol (SCAP) 安全内容自动化协议
- Software Supply Chain Security Guidance
- Supply chain Levels for Software Artifacts, or SLSA (salsa)
- sigstore Software Supply Chain Security
- OpenSSF Open Source Security Foundation
[编辑] 服务
- Formal Verification(形式化验证) for Blockchain & Smart Contracts and Software & Hardware
- Zero Trust Architecture(零信任架构)
- Security Analytics(安全分析)
- Intrusion Detection(入侵检测)
- Log Data Analysis(日志数据分析)
- File Integrity Monitoring(文件完整性监控)
- Vulnerability Detection(漏洞检测)
- Configuration Assessment(配置评估)
- Incident Response(应急响应)
- Regulatory Compliance(合规性)
- Cloud Security Monitoring(云安全监控)
- Container Security(容器安全)Kubernetes Security 风险分析、安全合规、RBAC可视化和image漏洞扫描 CNCF Security Technical Advisory Group
- Database Security(数据库安全)
- Mobile Security(移动安全) OWASP Mobile Application Security Verification Standard (MASVS)
[编辑] 运营支撑
C# Web/API + C++/Qt 桌面 + PostgreSQL 数据存储是整个产品和技术体系的软件基础设施。
[编辑] 图集
[编辑] 链接
- Runtime Verification Inc We love formal methods
- OWASP
- Awesome Hacking
- Contrast
- Sonatype Automate DevSecOps
- 网络安全类公众号推荐
- Azure Key Vault